Setting up a secure and efficient SSH remote IoT Raspberry Pi system can revolutionize how you manage and interact with your smart devices. Whether you're a hobbyist or a professional developer, understanding the best practices for SSH remote access is essential. This guide will walk you through everything you need to know about optimizing your IoT Raspberry Pi setup using SSH.
SSH, or Secure Shell, is a cryptographic network protocol that allows secure communication between devices over an unsecured network. For IoT enthusiasts, leveraging SSH for remote access to Raspberry Pi offers unparalleled flexibility and control. In this article, we'll explore why SSH is the best solution for managing IoT devices and provide step-by-step instructions to set it up effectively.
As more people adopt IoT devices, the demand for secure remote access solutions continues to grow. With Raspberry Pi's affordability and versatility, it has become one of the most popular platforms for IoT projects. This comprehensive guide aims to equip you with the knowledge and tools necessary to create a robust SSH remote IoT Raspberry Pi setup.
Read also:Mark Arnold The Ultimate Guide To His Life Career And Achievements
Table of Contents
Introduction to SSH Remote Access
Raspberry Pi Overview and Its Role in IoT
Benefits of Using SSH for IoT Raspberry Pi
The Setup Process for SSH Remote IoT Raspberry Pi
Securing Your SSH Remote IoT Raspberry Pi
Troubleshooting Tips for SSH Remote IoT Raspberry Pi
Read also:Jeremy Fowler News Unveiling The Insider Stories And Expert Analysis
Advanced Features and Customizations
Common Mistakes to Avoid in SSH Setup
Alternatives to SSH for IoT Raspberry Pi
Introduction to SSH Remote Access
SSH remote access is a fundamental tool for managing IoT devices like the Raspberry Pi. By enabling secure communication, SSH ensures that your device remains protected from unauthorized access while allowing you to control it from anywhere in the world. This section explores the basics of SSH and why it's considered the best solution for IoT Raspberry Pi setups.
SSH operates on port 22 by default and uses encryption to protect data transmitted between the client and server. When setting up an IoT Raspberry Pi, SSH provides a reliable method for accessing your device remotely without compromising security. Whether you're configuring sensors, deploying scripts, or monitoring logs, SSH ensures seamless connectivity.
Why SSH is Preferred for IoT Devices
Here are some reasons why SSH is the preferred choice for IoT Raspberry Pi setups:
- End-to-end encryption ensures secure communication.
- Supports authentication methods such as password and SSH keys.
- Compatible with a wide range of operating systems and platforms.
- Lightweight and resource-efficient, ideal for IoT devices.
Raspberry Pi Overview and Its Role in IoT
The Raspberry Pi is a compact, single-board computer designed for educational purposes but has gained immense popularity among IoT enthusiasts. Its affordability, versatility, and ease of use make it an excellent choice for building IoT projects. In this section, we'll discuss how Raspberry Pi fits into the IoT ecosystem and why it's perfect for SSH-based remote access.
Raspberry Pi runs on various operating systems, including Raspberry Pi OS, which is optimized for IoT applications. By combining SSH remote access with Raspberry Pi's capabilities, users can manage their IoT devices efficiently, even from remote locations. This setup is particularly useful for monitoring environmental conditions, automating home systems, or deploying industrial IoT solutions.
Key Features of Raspberry Pi for IoT
- Low power consumption, ideal for long-term deployments.
- GPIO pins for interfacing with sensors and actuators.
- Support for wireless communication protocols like Wi-Fi and Bluetooth.
- Scalable storage options for data logging and processing.
Benefits of Using SSH for IoT Raspberry Pi
Using SSH for IoT Raspberry Pi setups offers numerous advantages that make it the best solution for remote device management. This section outlines the primary benefits of leveraging SSH in your IoT projects.
One of the most significant advantages of SSH is its ability to provide secure, encrypted communication. Unlike other protocols, SSH ensures that your data remains protected from interception and tampering. Additionally, SSH supports advanced authentication methods, such as public-key cryptography, which enhance security further.
Top Benefits of SSH for IoT
- Secure communication through encryption.
- Support for advanced authentication methods.
- Compatibility with a wide range of IoT applications.
- Efficient resource utilization on IoT devices.
The Setup Process for SSH Remote IoT Raspberry Pi
Setting up SSH for remote access on your IoT Raspberry Pi involves several straightforward steps. This section provides a detailed guide to help you configure SSH on your Raspberry Pi device.
First, ensure that your Raspberry Pi is running the latest version of Raspberry Pi OS. Once updated, enable SSH by navigating to the Raspberry Pi Configuration tool. You can also enable SSH via the terminal by running the command:
sudo raspi-config
Step-by-Step SSH Setup
- Enable SSH on your Raspberry Pi through the configuration tool.
- Generate SSH keys for secure authentication.
- Set up port forwarding on your router for remote access.
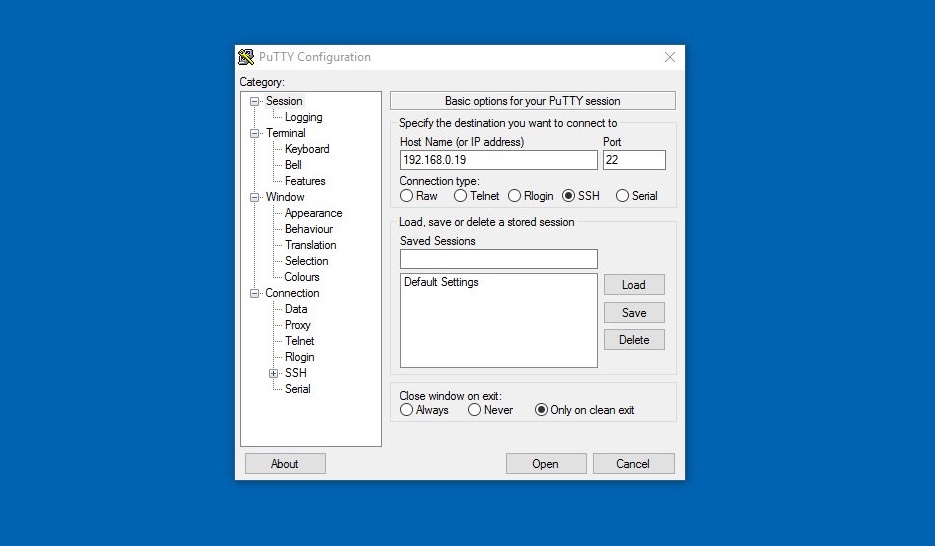
- Test the connection using an SSH client like PuTTY or Terminal.
Securing Your SSH Remote IoT Raspberry Pi
While SSH is inherently secure, additional measures can further enhance the protection of your IoT Raspberry Pi setup. This section discusses best practices for securing your SSH remote access.
One effective method is to disable password authentication and rely solely on SSH keys. This approach minimizes the risk of brute-force attacks and unauthorized access. Additionally, consider changing the default SSH port (22) to a non-standard port to reduce automated attack attempts.
Security Best Practices
- Use SSH keys instead of passwords for authentication.
- Change the default SSH port to a non-standard value.
- Limit SSH access to specific IP addresses or networks.
- Regularly update your Raspberry Pi OS and SSH software.
Troubleshooting Tips for SSH Remote IoT Raspberry Pi
Even with a well-configured SSH setup, issues may arise during remote access. This section provides troubleshooting tips to help you resolve common problems related to SSH remote IoT Raspberry Pi setups.
One common issue is connection timeouts, which can occur due to network instability or incorrect port forwarding configurations. To troubleshoot, verify that your router settings allow SSH traffic and ensure that your Raspberry Pi's IP address is correctly configured.
Common Troubleshooting Steps
- Check your router's port forwarding settings.
- Verify the SSH service is running on your Raspberry Pi.
- Test the connection using different network environments.
- Review SSH logs for detailed error messages.
Advanced Features and Customizations
Once you've mastered the basics of SSH remote IoT Raspberry Pi setups, you can explore advanced features and customizations to enhance your system's functionality. This section highlights some of the most useful advanced SSH features.
Tunneling is one such feature that allows you to securely access other services running on your Raspberry Pi. For example, you can use SSH tunneling to access a web server or database running on your IoT device. Additionally, SSH supports automation through scripts, enabling you to perform repetitive tasks efficiently.
Exploring Advanced SSH Features
- Set up SSH tunneling for secure service access.
- Automate tasks using SSH scripts and cron jobs.
- Implement two-factor authentication for added security.
- Monitor SSH activity using logging and analytics tools.
Common Mistakes to Avoid in SSH Setup
While SSH is a powerful tool, improper configuration can lead to security vulnerabilities and operational issues. This section outlines common mistakes to avoid when setting up SSH for your IoT Raspberry Pi.
One frequent mistake is neglecting to update SSH software, which can leave your system exposed to known vulnerabilities. Another common error is relying solely on password authentication, which increases the risk of brute-force attacks. To avoid these pitfalls, always keep your software updated and use SSH keys for authentication.
Avoid These Common SSH Mistakes
- Do not use default SSH settings without customization.
- Avoid using weak passwords or no authentication at all.
- Regularly review and update your SSH configurations.
- Test your setup thoroughly before deploying it in production.
Alternatives to SSH for IoT Raspberry Pi
While SSH is the best solution for most IoT Raspberry Pi setups, alternative remote access methods exist. This section examines some of these alternatives and their suitability for IoT applications.
One popular alternative is VNC (Virtual Network Computing), which allows graphical remote access to your Raspberry Pi. However, VNC consumes more resources than SSH and may not be suitable for lightweight IoT devices. Another option is MQTT, a lightweight messaging protocol ideal for IoT data transfer but lacks the robustness of SSH for general remote access.
Comparison of SSH Alternatives
- VNC: Graphical remote access but resource-intensive.
- MQTT: Lightweight messaging protocol for IoT data transfer.
- Web-based interfaces: Easy to use but may compromise security.
Conclusion and Next Steps
In conclusion, setting up a secure SSH remote IoT Raspberry Pi system is essential for managing and interacting with your smart devices effectively. By following the best practices outlined in this guide, you can ensure that your setup remains protected while providing seamless remote access.
We encourage you to take action by implementing the steps discussed in this article. Whether you're configuring SSH for the first time or exploring advanced features, your IoT Raspberry Pi setup will benefit from these insights. Share your thoughts and experiences in the comments below, and don't forget to explore other articles on our site for more IoT tips and tricks.
For further reading, consider checking out the official Raspberry Pi documentation and SSH best practices guides from trusted sources such as the OpenSSH website and Raspberry Pi Foundation.