SSH IoT applications are revolutionizing the way we interact with connected devices in both personal and professional environments. As the Internet of Things (IoT) continues to grow exponentially, secure communication between devices has become a critical requirement. Secure Shell (SSH) provides an encrypted and reliable method for managing IoT devices remotely, ensuring data integrity and privacy. This article delves into the world of SSH IoT applications, exploring their benefits, implementation, and best practices.
The rise of IoT has transformed industries, from manufacturing to healthcare and beyond. However, with this rapid expansion comes the challenge of securing the vast network of interconnected devices. SSH IoT applications offer a robust solution to these security concerns by providing encrypted channels for device communication and management. Understanding how to leverage SSH in IoT ecosystems is essential for organizations and individuals alike.
In this guide, we will explore the fundamentals of SSH, its applications in IoT, and practical implementation strategies. Whether you're a developer, IT professional, or simply curious about IoT security, this article will equip you with the knowledge to harness the power of SSH IoT applications effectively. Let's dive in!
Read also:Is Kenny Loggins Married Today A Complete Overview Of His Marital Status
Table of Contents
- What is SSH?
- SSH in IoT: An Overview
- Key Benefits of SSH IoT Applications
- Implementation Steps for SSH IoT
- Security Considerations in SSH IoT Applications
- Real-World Applications of SSH IoT
- Challenges and Solutions in SSH IoT Deployment
- Optimizing Performance of SSH IoT Systems
- Future Trends in SSH IoT Technology
- Conclusion
What is SSH?
Secure Shell (SSH) is a cryptographic network protocol designed for secure data communication over unsecured networks. It provides a secure channel for remote login and other secure network services. SSH ensures data integrity, confidentiality, and authentication through encryption and public-key cryptography. Originally developed in 1995, SSH has become an industry standard for secure communication, particularly in IT infrastructure management.
How SSH Works
SSH operates by establishing an encrypted connection between a client and a server. The protocol uses public-key cryptography for authentication and symmetric encryption for data transfer. Key components of SSH include:
- SSH Client: The software used to initiate a connection to an SSH server.
- SSH Server: The software running on the target machine to accept and manage SSH connections.
- Encryption Algorithms: SSH supports various encryption methods, such as AES and RSA, to secure data transmission.
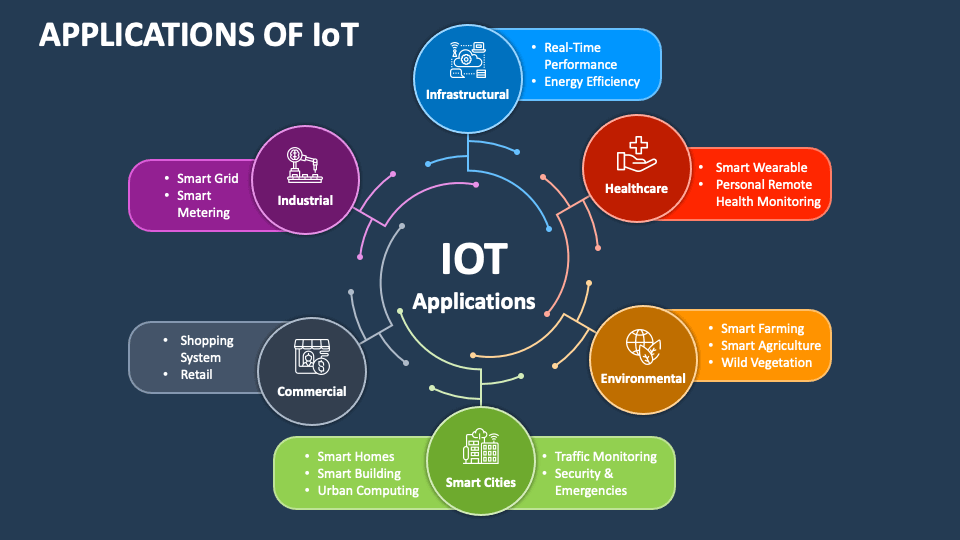
SSH in IoT: An Overview
SSH IoT applications leverage the power of Secure Shell to enhance security in Internet of Things ecosystems. As IoT devices are often deployed in remote or unsecured environments, ensuring secure communication is paramount. SSH provides a reliable solution for managing and monitoring IoT devices, enabling administrators to perform tasks such as firmware updates, configuration changes, and data retrieval securely.
Why SSH is Ideal for IoT
SSH is particularly well-suited for IoT applications due to its:
- Strong encryption capabilities.
- Robust authentication mechanisms.
- Compatibility with a wide range of devices and operating systems.
Key Benefits of SSH IoT Applications
Implementing SSH in IoT ecosystems offers numerous advantages, including:
- Data Security: SSH ensures that data transmitted between IoT devices remains confidential and tamper-proof.
- Remote Access: Administrators can securely manage IoT devices from anywhere, streamlining operations and reducing downtime.
- Scalability: SSH can handle large-scale IoT deployments, making it suitable for enterprise-level applications.
Implementation Steps for SSH IoT
Setting up SSH IoT applications involves several key steps:
Read also:Discover The Magic Of Amc Classic Grand Prairie 18 Your Ultimate Movie Experience
- Device Configuration: Install and configure SSH server software on IoT devices.
- Key Generation: Generate public and private keys for secure authentication.
- Network Setup: Configure network settings to allow SSH traffic while maintaining security.
- Testing and Validation: Test the SSH connection to ensure proper functionality and security.
Best Practices for Implementation
To maximize the effectiveness of SSH IoT applications, consider the following best practices:
- Regularly update SSH software to address security vulnerabilities.
- Use strong, unique passwords and key pairs for authentication.
- Monitor SSH activity for unauthorized access attempts.
Security Considerations in SSH IoT Applications
While SSH enhances security in IoT ecosystems, it is not without its challenges. Key security considerations include:
- Key Management: Properly managing SSH keys is crucial to prevent unauthorized access.
- Vulnerability Patching: Keeping SSH software up-to-date is essential to protect against known vulnerabilities.
- Network Segmentation: Isolating IoT devices on separate networks can reduce the risk of attacks.
Addressing Common Security Threats
Common security threats in SSH IoT applications include brute-force attacks, man-in-the-middle attacks, and key theft. Implementing measures such as two-factor authentication, network monitoring, and regular security audits can help mitigate these risks.
Real-World Applications of SSH IoT
SSH IoT applications are already being used in various industries to enhance security and efficiency. Some notable examples include:
- Smart Grids: SSH enables secure communication between smart meters and utility providers, ensuring accurate data collection and billing.
- Healthcare: SSH is used to secure the transmission of sensitive medical data between IoT devices in hospitals and clinics.
- Manufacturing: SSH facilitates remote monitoring and control of industrial IoT devices, improving productivity and reducing maintenance costs.
Case Studies
Several organizations have successfully implemented SSH IoT applications to address specific challenges. For instance, a leading energy provider used SSH to secure communications in its smart grid infrastructure, resulting in improved reliability and customer satisfaction.
Challenges and Solutions in SSH IoT Deployment
Deploying SSH IoT applications can present several challenges, including:
- Resource Constraints: Many IoT devices have limited processing power and memory, making it challenging to implement complex encryption algorithms.
- Key Management Complexity: Managing SSH keys across large IoT networks can be cumbersome without proper tools and processes.
Possible Solutions
To overcome these challenges, organizations can adopt solutions such as lightweight encryption protocols and automated key management systems. Collaborating with experienced IT security professionals can also help ensure a successful deployment.
Optimizing Performance of SSH IoT Systems
To ensure optimal performance of SSH IoT applications, consider the following strategies:
- Use compression to reduce data transfer overhead.
- Optimize SSH configuration settings for specific use cases.
- Regularly monitor system performance and address bottlenecks as needed.
Performance Monitoring Tools
Utilizing performance monitoring tools can help identify and resolve issues before they impact system functionality. Popular tools for SSH performance monitoring include Nagios and Zabbix.
Future Trends in SSH IoT Technology
The future of SSH IoT applications looks promising, with advancements in technology driving innovation. Key trends to watch include:
- Quantum-Safe Cryptography: As quantum computing becomes more prevalent, SSH will need to adopt quantum-resistant encryption methods.
- AI-Powered Security: Artificial intelligence will play a significant role in detecting and responding to security threats in SSH IoT systems.
- Edge Computing Integration: Combining SSH with edge computing will enhance the scalability and efficiency of IoT networks.
Conclusion
SSH IoT applications offer a powerful solution for securing communication in Internet of Things ecosystems. By leveraging the robust features of Secure Shell, organizations can protect sensitive data, enable remote device management, and enhance overall system security. As IoT continues to evolve, staying informed about the latest trends and best practices in SSH IoT technology will be critical for success.
We encourage you to explore the possibilities of SSH IoT applications further and share your thoughts in the comments below. For more insights into IoT security and related topics, check out our other articles on the website. Together, let's build a safer, smarter connected world!