In today's digital era, remotely access SSH web has become an essential skill for IT professionals and remote workers alike. Secure Shell (SSH) is one of the most reliable methods to access servers and manage systems from anywhere in the world. Whether you're a developer, system administrator, or simply someone looking to enhance your cybersecurity knowledge, understanding SSH remote access is crucial. This guide will provide you with step-by-step instructions and expert tips to help you master this technique.
With more organizations adopting remote work models, the demand for secure and efficient remote access solutions has surged. SSH offers a robust encryption protocol that ensures your data remains protected while accessing web-based systems. This article aims to equip you with the knowledge to set up, configure, and troubleshoot SSH connections effectively.
By the end of this guide, you will have a deep understanding of how SSH works, the tools required for remote access, and practical steps to implement secure connections. Whether you're a beginner or an experienced professional, this article will provide valuable insights to enhance your skills in remotely accessing SSH web systems.
Read also:Jesiree Dizon Kids A Comprehensive Guide To Family Life Parenting And Influence
Below is a detailed table of contents to help you navigate through the article easily:
Table of Contents
- Introduction to SSH
- Why Choose SSH for Remote Access
- Setting Up SSH
- Configuring SSH for Web Access
- Securing Your SSH Connection
- Troubleshooting SSH Issues
- Best Practices for Remote SSH Access
- Alternatives to SSH
- Real-World Applications of SSH
- Conclusion
Introduction to SSH
Secure Shell (SSH) is a cryptographic network protocol designed to secure data communication over unsecured networks. It provides a secure channel for remote access to servers and systems, ensuring that all transmitted data is encrypted and protected from unauthorized access. SSH is widely used in web development, server management, and network administration due to its robust security features.
The primary function of SSH is to allow users to log into remote machines and execute commands securely. It supports various authentication methods, including password-based and public-key authentication, making it versatile for different use cases. Additionally, SSH can be used for file transfers, tunneling, and port forwarding, enhancing its utility in web-based environments.
Why Choose SSH for Remote Access
When considering methods for remotely accessing web servers, SSH stands out due to its numerous advantages. Firstly, SSH employs strong encryption algorithms to protect data during transmission, ensuring that sensitive information remains confidential. Secondly, its support for public-key authentication eliminates the need for passwords, reducing the risk of brute-force attacks.
Moreover, SSH is compatible with a wide range of operating systems and platforms, making it accessible to users regardless of their technical environment. Its ability to create secure tunnels for other protocols further enhances its versatility, allowing users to access web applications securely through SSH connections.
Setting Up SSH
Installing SSH Client and Server
To begin using SSH for remote access, you need to install both the SSH client and server software. On Linux and macOS systems, SSH is usually pre-installed, but you may need to enable the SSH server if it's not running. For Windows users, you can install SSH using tools like OpenSSH or third-party software such as PuTTY.
Read also:Torture Belly Button Understanding The Risks Impacts And Prevention
- Linux: Use the command
sudo apt install openssh-serverto install the SSH server. - macOS: Enable the SSH server by going to System Preferences > Sharing > Remote Login.
- Windows: Download and install OpenSSH from the Microsoft Store or use PuTTY for SSH client functionality.
Once installed, ensure that the SSH service is running and configured correctly. You can check the status of the SSH server by running systemctl status ssh on Linux systems.
Configuring SSH for Web Access
Configuring SSH for web access involves setting up port forwarding to allow secure connections to web-based applications. This process typically requires modifying the SSH configuration file, located at /etc/ssh/sshd_config on most systems.
Key configurations include:
- Setting the listening port (default is 22).
- Enabling or disabling root login.
- Specifying allowed users or groups.
After making changes to the configuration file, restart the SSH service to apply the new settings. This ensures that your SSH server is optimized for secure web access.
Securing Your SSH Connection
Using SSH Keys
One of the most effective ways to secure your SSH connection is by using SSH keys instead of passwords. SSH keys provide a more secure authentication method, as they are nearly impossible to brute-force. To generate SSH keys, use the following command:
ssh-keygen -t rsa -b 4096
This command generates a 4096-bit RSA key pair, which you can then copy to the remote server using:
ssh-copy-id user@remote-server
Disabling Password Authentication
Once you have set up SSH keys, it is advisable to disable password authentication to further enhance security. This can be done by editing the SSH configuration file and setting the following parameter:
PasswordAuthentication no
After saving the changes, restart the SSH service to enforce the new security settings.
Troubleshooting SSH Issues
Despite its robustness, SSH connections can sometimes encounter issues. Common problems include connection timeouts, authentication failures, and misconfigured settings. To troubleshoot these issues, follow these steps:
- Check the SSH service status using
systemctl status ssh. - Verify the firewall settings to ensure that the SSH port is open.
- Review the SSH logs for error messages using
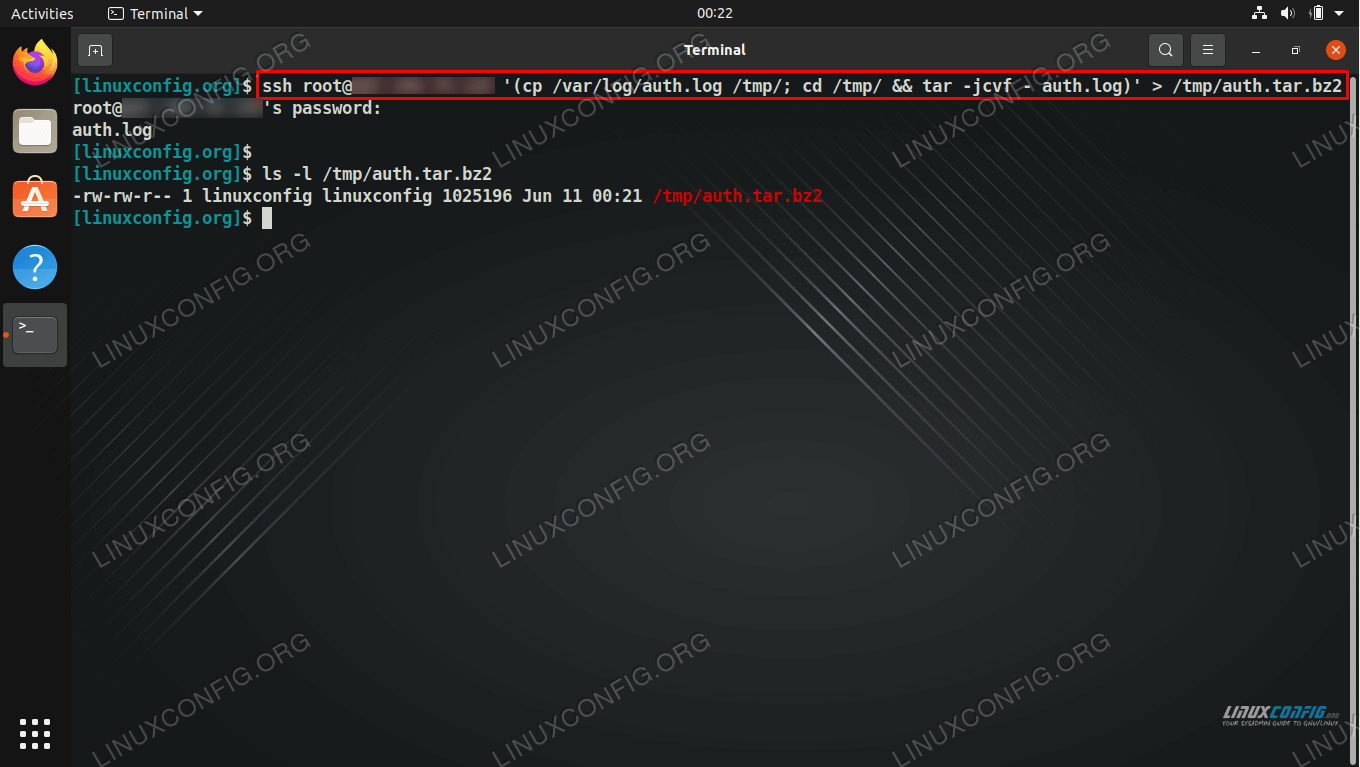
tail -f /var/log/auth.log.
By systematically addressing these potential issues, you can resolve most SSH connection problems effectively.
Best Practices for Remote SSH Access
To ensure the security and reliability of your SSH connections, follow these best practices:
- Regularly update your SSH software to the latest version.
- Use strong, unique SSH keys for authentication.
- Limit SSH access to trusted IP addresses using firewall rules.
- Monitor SSH logs for suspicious activity and potential threats.
Implementing these practices will help protect your systems from unauthorized access and potential security breaches.
Alternatives to SSH
While SSH is the most widely used protocol for secure remote access, there are alternative solutions available. These include:
- VPN: Virtual Private Networks create encrypted tunnels for secure access to web applications.
- RDP: Remote Desktop Protocol is commonly used for graphical remote access on Windows systems.
- SSL/TLS: Secure communication protocols used in web browsers for encrypted data transfer.
Each of these alternatives has its own strengths and limitations, making them suitable for different use cases.
Real-World Applications of SSH
SSH is widely used in various industries and applications, including:
- Web hosting and server management.
- DevOps automation and continuous integration.
- Secure file transfers using SFTP (SSH File Transfer Protocol).
- Network device configuration and monitoring.
Its versatility and security features make SSH an indispensable tool for professionals working in IT and cybersecurity fields.
Conclusion
In conclusion, mastering the art of remotely access SSH web is essential for anyone involved in web development, server management, or cybersecurity. By following the steps outlined in this guide, you can set up, configure, and secure your SSH connections effectively. Remember to adhere to best practices and stay updated with the latest security trends to protect your systems from potential threats.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, explore other articles on our site to deepen your knowledge of cybersecurity and related technologies. Together, let's build a safer digital world!