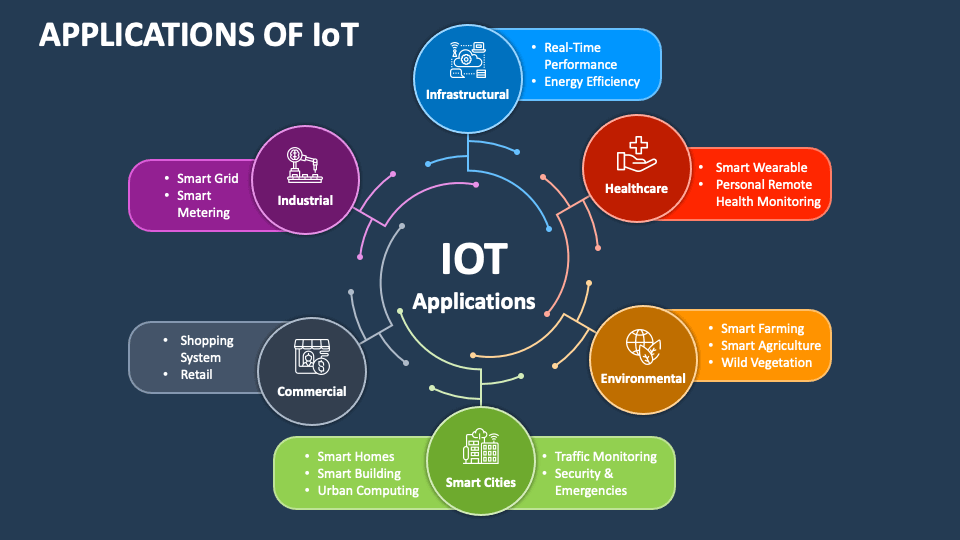
In today's hyperconnected world, the Internet of Things (IooT) continues to transform how devices interact and exchange information. IoT SSH applications play a pivotal role in ensuring secure communication between devices, making them indispensable in the modern digital landscape. These applications leverage the power of Secure Shell (SSH) protocols to provide robust security and reliability, enabling seamless interaction between IoT devices.
As IoT adoption continues to grow exponentially, understanding the intricacies of IoT SSH applications becomes crucial for both developers and end-users. From home automation systems to industrial control systems, these applications ensure that data remains protected while maintaining high levels of performance.
This comprehensive article delves deep into the world of IoT SSH applications, exploring their functionalities, benefits, challenges, and future prospects. Whether you're a tech enthusiast or a professional looking to enhance your knowledge, this guide will equip you with the essential information you need to navigate this evolving domain.
Read also:Tanning Spray Walgreens Your Ultimate Guide To Achieving A Flawless Glow
Table of Contents
- Introduction to IoT SSH Applications
- Benefits of IoT SSH Applications
- Security Considerations in IoT SSH
- Common Use Cases for IoT SSH
- Challenges in Implementing IoT SSH
- Future Trends in IoT SSH Applications
- Best Practices for Using IoT SSH
- Comparison with Other Protocols
- Industrial Applications of IoT SSH
- Conclusion
Introduction to IoT SSH Applications
IoT SSH applications represent a vital intersection between the Internet of Things and secure communication protocols. These applications utilize the Secure Shell (SSH) protocol to create a secure tunnel for data transfer between IoT devices. SSH, originally designed for securing remote access to network devices, has evolved to accommodate the unique needs of IoT ecosystems.
What is SSH?
Secure Shell, or SSH, is a cryptographic network protocol used for secure communication over unsecured networks. It provides features such as authentication, encryption, and integrity, making it an ideal choice for securing IoT communications. In the context of IoT, SSH ensures that sensitive data transmitted between devices remains protected from unauthorized access and tampering.
Why IoT SSH Matters
As the number of connected devices increases, so does the risk of cyber threats. IoT SSH applications address these concerns by offering a secure, reliable, and efficient method for device communication. They play a critical role in safeguarding data integrity and privacy in an increasingly interconnected world.
Benefits of IoT SSH Applications
Implementing IoT SSH applications brings numerous advantages to both individuals and organizations. Below are some of the key benefits:
Read also:Is Neil Flynn Married In Real Life Discover The Truth About His Personal Life
- Enhanced Security: IoT SSH applications provide robust encryption and authentication mechanisms, ensuring that data remains secure during transmission.
- Improved Reliability: By leveraging SSH's reliable connection protocols, IoT devices can maintain stable communication even in challenging network conditions.
- Scalability: These applications are designed to handle large-scale IoT deployments, making them suitable for enterprise-level solutions.
- Interoperability: IoT SSH applications support seamless integration with various devices and platforms, promoting flexibility and adaptability.
Security Considerations in IoT SSH
While IoT SSH applications offer significant security benefits, they also come with certain challenges that must be addressed. Below are some key security considerations:
Authentication Mechanisms
Implementing strong authentication protocols is essential to prevent unauthorized access to IoT devices. This includes using public key infrastructure (PKI) and multi-factor authentication (MFA) to enhance security.
Data Encryption
Encrypting data during transmission is crucial to protect sensitive information from interception. IoT SSH applications employ advanced encryption algorithms to ensure data confidentiality.
Regular Updates
Keeping IoT SSH applications updated with the latest security patches is vital to address emerging threats and vulnerabilities.
Common Use Cases for IoT SSH
IoT SSH applications find applications across various industries. Below are some common use cases:
- Smart Homes: Securing communication between smart devices in home automation systems.
- Healthcare: Protecting patient data in IoT-enabled medical devices.
- Industrial Automation: Ensuring secure communication in industrial control systems.
- Transportation: Safeguarding data in connected vehicles and transportation infrastructure.
Challenges in Implementing IoT SSH
Despite their numerous advantages, implementing IoT SSH applications comes with its own set of challenges. Below are some common obstacles:
Resource Constraints
Many IoT devices have limited processing power and memory, making it challenging to implement resource-intensive SSH protocols.
Complexity
Configuring and managing IoT SSH applications can be complex, requiring specialized knowledge and skills.
Interoperability Issues
Ensuring compatibility between different devices and platforms can be a significant challenge in IoT SSH implementations.
Future Trends in IoT SSH Applications
The future of IoT SSH applications looks promising, with several emerging trends set to shape the landscape:
- Quantum-Resistant Cryptography: As quantum computing becomes a reality, IoT SSH applications will need to adopt quantum-resistant encryption methods.
- AI Integration: Incorporating artificial intelligence (AI) into IoT SSH applications can enhance security and improve operational efficiency.
- Edge Computing: Leveraging edge computing can reduce latency and improve performance in IoT SSH implementations.
Best Practices for Using IoT SSH
To maximize the benefits of IoT SSH applications, it's essential to follow best practices. Below are some recommendations:
- Use Strong Passwords: Implement complex passwords and regularly update them to enhance security.
- Implement Key-Based Authentication: Utilize public key authentication to reduce the risk of brute-force attacks.
- Monitor Activity Logs: Regularly review activity logs to detect and respond to suspicious activities promptly.
Comparison with Other Protocols
IoT SSH applications offer distinct advantages over other communication protocols. Below is a comparison with some commonly used protocols:
MQTT vs. IoT SSH
While MQTT is lightweight and ideal for constrained environments, IoT SSH provides stronger security features, making it more suitable for sensitive applications.
HTTP vs. IoT SSH
HTTP is widely used for web communication but lacks the robust security features of IoT SSH, making the latter a better choice for securing IoT communications.
Industrial Applications of IoT SSH
In the industrial sector, IoT SSH applications play a crucial role in ensuring secure communication between devices. Below are some key applications:
- Remote Monitoring: Enabling secure remote access to industrial equipment for monitoring and maintenance.
- Supply Chain Management: Securing communication between IoT devices used in supply chain tracking and logistics.
- Energy Management: Protecting data in smart grid systems and energy management solutions.
Conclusion
In conclusion, IoT SSH applications represent a vital component of the modern IoT ecosystem, offering robust security and reliability for device communication. By understanding their functionalities, benefits, and challenges, individuals and organizations can harness the full potential of these applications to enhance their IoT deployments.
We invite you to share your thoughts and experiences with IoT SSH applications in the comments section below. Additionally, feel free to explore other articles on our website to deepen your knowledge of IoT and related technologies.