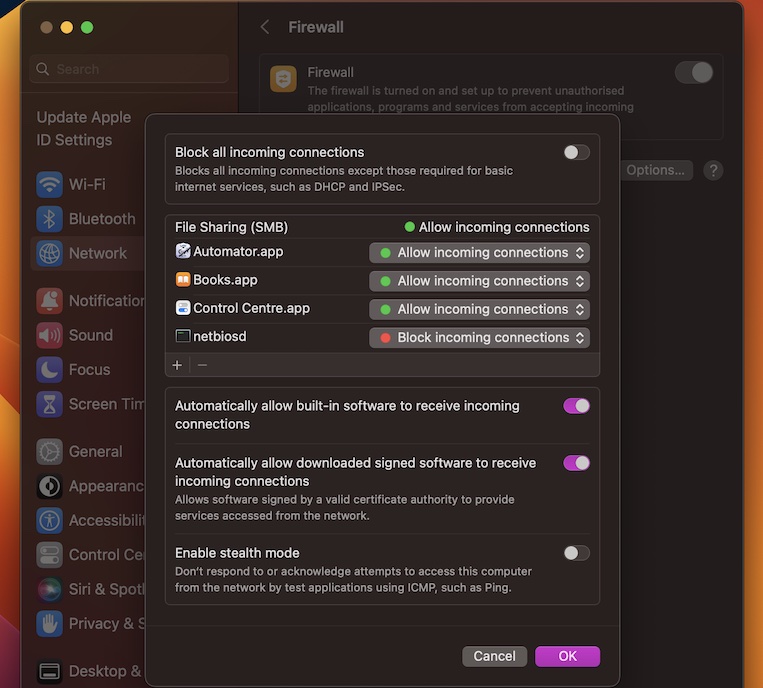
Using RemoteIoT behind a firewall on Mac can seem daunting, but with the right strategies, it’s entirely achievable. As more businesses and individuals rely on IoT devices, understanding how to securely connect to these devices from behind a firewall is crucial. This article will guide you step-by-step through the process, ensuring your network remains secure while maintaining optimal performance.
RemoteIoT technology allows you to access and manage IoT devices from remote locations. However, firewalls often act as barriers, making it challenging to establish seamless connections. This guide will address common issues and provide practical solutions to help you navigate this complex environment.
Whether you're a network administrator, a tech enthusiast, or simply someone looking to enhance their IoT capabilities, this article is designed to equip you with the knowledge and tools necessary to use RemoteIoT effectively. Let’s dive in and explore how you can achieve this without compromising security.
Read also:Gina Torres Boyfriend A Complete Guide To Her Love Life And Relationships
Table of Contents
- Introduction to RemoteIoT
- Firewall Challenges with RemoteIoT
- Mac-Specific Considerations
- Setup Process for RemoteIoT Behind Firewall
- Security Measures to Protect Your Network
- Tools and Software Recommendations
- Troubleshooting Tips for Common Issues
- Performance Optimization Techniques
- Legal and Ethical Considerations
- Conclusion
Introduction to RemoteIoT
RemoteIoT refers to the ability to control and monitor Internet of Things (IoT) devices from a remote location. This technology has revolutionized industries by enabling real-time data collection and analysis. However, integrating RemoteIoT into a network protected by a firewall requires careful planning.
What is RemoteIoT?
RemoteIoT encompasses all the tools and technologies that allow users to interact with IoT devices remotely. It includes software platforms, communication protocols, and security measures designed to ensure seamless connectivity.
Why Use RemoteIoT?
- Enhanced productivity through real-time monitoring.
- Cost savings by reducing the need for on-site visits.
- Improved data accuracy and reliability.
Firewall Challenges with RemoteIoT
Firewalls are designed to protect networks from unauthorized access, but they can also block legitimate RemoteIoT connections. Understanding these challenges is the first step in overcoming them.
Common Firewall Issues
- Port blocking: Firewalls often block specific ports required for RemoteIoT communication.
- IP restrictions: Some firewalls restrict access based on IP addresses, making it difficult to establish connections from unknown locations.
- Encryption requirements: Firewalls may require encrypted connections, which can complicate the setup process.
Mac-Specific Considerations
Using RemoteIoT on a Mac introduces unique considerations due to differences in operating systems and network configurations.
MacOS Firewall Settings
MacOS comes with its own firewall settings that can either complement or conflict with your network’s firewall. Adjusting these settings appropriately is essential for successful RemoteIoT implementation.
Recommended Mac Applications
- Tunnelblick: A popular open-source application for setting up VPNs on Mac.
- Network Utility: A built-in tool for troubleshooting network issues.
Setup Process for RemoteIoT Behind Firewall
The setup process involves several key steps to ensure a secure and functional RemoteIoT connection.
Read also:Emily Van Camp A Journey Through Her Career Life And Legacy
Step 1: Assess Your Network Configuration
Begin by evaluating your current network setup, including firewall rules and available ports. This assessment will help identify potential obstacles.
Step 2: Configure Firewall Rules
Adjust your firewall settings to allow RemoteIoT traffic while maintaining security. This may involve opening specific ports or creating exceptions for trusted IP addresses.
Step 3: Implement Encryption
Use encryption protocols such as SSL/TLS to secure your RemoteIoT connections. This step is crucial for protecting sensitive data transmitted between devices.
Security Measures to Protect Your Network
Securing your network is paramount when using RemoteIoT behind a firewall. Here are some best practices to consider:
Regular Security Audits
Conduct regular audits to identify and address vulnerabilities in your network. This proactive approach helps prevent unauthorized access and data breaches.
User Authentication
Implement strong user authentication mechanisms, such as two-factor authentication (2FA), to ensure only authorized users can access your RemoteIoT devices.
Tools and Software Recommendations
Several tools and software solutions can facilitate the use of RemoteIoT behind a firewall on Mac:
VPN Solutions
- OpenVPN: A versatile and secure option for establishing encrypted connections.
- WireGuard: Known for its simplicity and high performance.
Monitoring Tools
- PRTG Network Monitor: Offers comprehensive network monitoring capabilities.
- Zabbix: A powerful open-source tool for monitoring IoT devices and networks.
Troubleshooting Tips for Common Issues
Even with careful planning, issues may arise. Here are some troubleshooting tips to help you resolve common problems:
Connection Failures
Check your firewall logs for any blocked connections and adjust rules accordingly. Ensure all necessary ports are open and properly configured.
Performance Degradation
Monitor network traffic to identify bottlenecks or excessive latency. Optimizing your network settings can improve overall performance.
Performance Optimization Techniques
Optimizing performance is essential for maintaining efficient RemoteIoT operations. Consider the following techniques:
Bandwidth Management
Allocate bandwidth strategically to prioritize critical RemoteIoT communications. This ensures smooth operation even during peak usage times.
Device Updates
Regularly update your IoT devices and software to benefit from the latest features and security patches. This practice enhances both performance and security.
Legal and Ethical Considerations
Using RemoteIoT behind a firewall also involves legal and ethical responsibilities. Ensure compliance with relevant regulations and respect user privacy.
Data Privacy Laws
Familiarize yourself with data protection laws such as GDPR and CCPA. Implement measures to safeguard personal data collected by your IoT devices.
Responsible Usage
Use RemoteIoT technology responsibly, avoiding any actions that could harm or compromise other networks. Ethical considerations are just as important as technical ones.
Conclusion
Using RemoteIoT behind a firewall on Mac is achievable with the right approach and tools. By following the steps outlined in this guide, you can establish secure and efficient connections while maintaining network integrity. Remember to prioritize security, regularly update your systems, and adhere to legal and ethical standards.
We encourage you to share your experiences and insights in the comments section below. Additionally, feel free to explore other articles on our site for more valuable information on IoT and network security. Together, let’s build a safer and more connected digital world!