In today's era of interconnected devices, remote IoT (Internet of Things) management has become essential for businesses and individuals alike. Remote IoT device SSH tutorial offers a reliable way to access and manage IoT devices securely over the internet. Whether you're setting up a smart home system or managing industrial sensors, understanding SSH (Secure Shell) protocols is crucial for maintaining device security and efficiency.
SSH provides a secure channel for remote communication between devices, ensuring that sensitive data remains protected from unauthorized access. This tutorial will guide you step-by-step on how to connect to your IoT devices using SSH, configure settings, troubleshoot common issues, and implement best practices for secure remote access.
By the end of this article, you'll have a solid understanding of the technical aspects of SSH in IoT, as well as practical tips to enhance your device's security. Let's dive in and explore the world of remote IoT management!
Read also:Rose Hart Ed A Comprehensive Guide To Understanding And Appreciating The Legacy
Table of Contents
- Introduction to SSH
- Why Use SSH for IoT Devices?
- Setting Up SSH on IoT Devices
- Connecting to a Remote IoT Device
- Securing Your SSH Connection
- Troubleshooting Common SSH Issues
- Advanced SSH Configurations
- Best Practices for SSH in IoT
- Real-World Applications of SSH in IoT
- Conclusion
Introduction to SSH
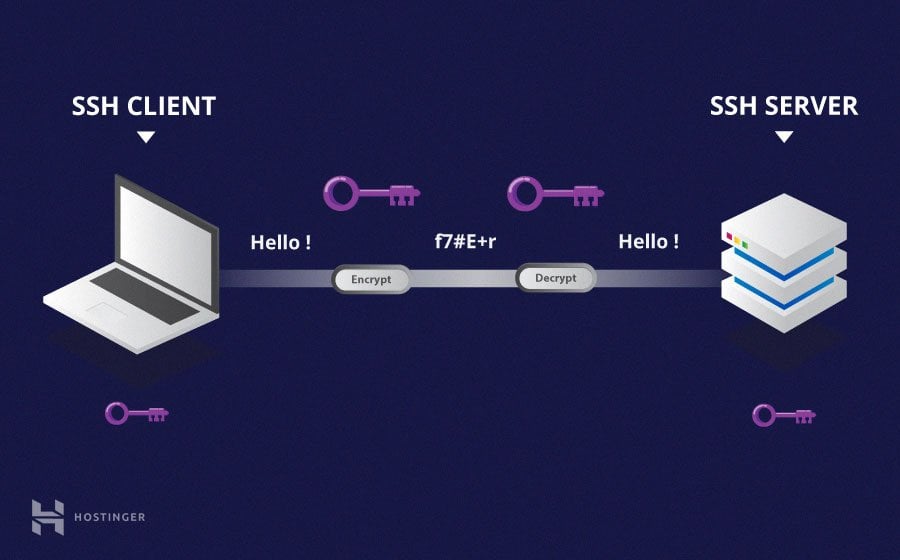
SSH, or Secure Shell, is a cryptographic network protocol that facilitates secure communication between devices over an unsecured network. It encrypts all data transferred between the client and server, ensuring confidentiality, integrity, and authentication. In the context of IoT, SSH allows users to remotely access and manage devices without compromising their security.
How SSH Works
SSH operates on a client-server model, where the client initiates a connection to the server. The process involves:
- Authentication: Users authenticate themselves using passwords, public key cryptography, or other methods.
- Encryption: Data is encrypted during transmission to prevent interception by malicious actors.
- Session Management: Once authenticated, users can execute commands, transfer files, or manage configurations.
Advantages of SSH
Some key benefits of using SSH include:
- Secure communication through encryption.
- Strong authentication mechanisms.
- Compatibility with various platforms and operating systems.
Why Use SSH for IoT Devices?
IoT devices often operate in environments where physical access is limited or impractical. SSH provides a robust solution for remote management, offering several advantages:
Enhanced Security
SSH encrypts all data exchanged between the client and server, making it difficult for attackers to intercept or manipulate the information. This is particularly important for IoT devices that handle sensitive data, such as healthcare monitors or financial systems.
Remote Accessibility
With SSH, administrators can access IoT devices from anywhere in the world, provided they have internet connectivity. This flexibility is invaluable for managing large-scale IoT deployments.
Read also:Exploring The Enigmatic World Of Sharkie Hells Belles
Automation Capabilities
SSH supports script automation, enabling users to automate repetitive tasks such as software updates, configuration changes, and data backups. This reduces manual effort and minimizes the risk of human error.
Setting Up SSH on IoT Devices
Before connecting to your IoT device via SSH, you need to ensure that SSH is properly configured on the device. Below are the steps to set up SSH on a typical IoT device:
Step 1: Enable SSH Service
Most IoT devices come with SSH disabled by default for security reasons. You'll need to enable it manually. For example, on a Raspberry Pi:
- Open the terminal.
- Run the command:
sudo raspi-config. - Navigate to "Interfacing Options"> "SSH"> "Enable".
Step 2: Configure Firewall Settings
Ensure that your firewall allows incoming SSH connections. Typically, SSH uses port 22. You can open this port using:
- For Linux:
sudo ufw allow 22. - For Windows Firewall: Add a rule to allow inbound traffic on port 22.
Step 3: Test Local Connection
Before attempting a remote connection, test SSH locally to ensure it's functioning correctly. Use the command:
ssh username@localhost.
Connecting to a Remote IoT Device
Once SSH is set up on your IoT device, you can connect to it remotely from another machine. Follow these steps:
Step 1: Obtain the Device's IP Address
Identify the IP address of your IoT device. You can use the command:
ifconfig(Linux/Mac) oripconfig(Windows).
Step 2: Establish the SSH Connection
From your client machine, open the terminal or SSH client and enter:
ssh username@device_ip_address.
Step 3: Authenticate
Enter your password or use a private key for authentication. If this is your first connection, you may need to accept the server's fingerprint.
Securing Your SSH Connection
While SSH is inherently secure, additional measures can enhance its protection against potential threats:
Use Public Key Authentication
Instead of relying on passwords, configure public key authentication. Generate a key pair using:
ssh-keygen.
Then, copy the public key to the IoT device:
ssh-copy-id username@device_ip_address.
Disable Password Authentication
Once public key authentication is set up, disable password-based login to prevent brute-force attacks. Edit the SSH configuration file:
sudo nano /etc/ssh/sshd_config.- Set
PasswordAuthentication no. - Restart the SSH service:
sudo service ssh restart.
Change the Default Port
Changing the default SSH port (22) can deter automated attacks. Modify the sshd_config file:
- Set
Port 2222(or any other unused port). - Update firewall rules to allow traffic on the new port.
Troubleshooting Common SSH Issues
Even with proper setup, SSH connections can sometimes fail. Below are some common issues and their solutions:
Connection Refused
This error usually occurs when the SSH service is not running or the port is blocked. Check:
- Whether SSH is enabled on the device.
- Firewall rules to ensure the port is open.
Authentication Failed
Double-check your username, password, and public key. Ensure there are no typos or mismatched keys.
Timeout Errors
Timeouts may occur due to network issues or incorrect IP addresses. Verify:
- Network connectivity.
- Device's IP address.
Advanced SSH Configurations
For advanced users, SSH offers various customization options to optimize performance and security:
SSH Tunneling
Create encrypted tunnels for secure data transfer. For example:
ssh -L local_port:destination_host:destination_port username@device_ip_address.
SSH Agent Forwarding
Enable agent forwarding to access other devices from the IoT device without re-authenticating. Add the following to your SSH configuration:
ForwardAgent yes.
Best Practices for SSH in IoT
Adopting best practices ensures the security and reliability of your SSH setup:
Regularly Update Software
Keep your IoT device's operating system and SSH software up to date to patch vulnerabilities.
Limit User Access
Restrict SSH access to trusted users and disable root login to minimize risks.
Monitor Logs
Regularly review SSH logs for suspicious activity. Use tools like logwatch or fail2ban to automate monitoring and block malicious IPs.
Real-World Applications of SSH in IoT
SSH is widely used in various IoT applications, including:
Smart Home Systems
SSH enables remote access to smart home devices, allowing users to monitor and control systems like lighting, temperature, and security cameras.
Industrial Automation
In manufacturing, SSH facilitates secure communication between sensors, controllers, and monitoring systems, ensuring smooth operations.
Healthcare Devices
SSH secures data transfer in medical IoT devices, protecting patient information and ensuring compliance with regulations.
Conclusion
This comprehensive remote IoT device SSH tutorial has covered everything you need to know about securely managing IoT devices using SSH. From setting up SSH on your device to implementing advanced configurations, you now have the tools to enhance your IoT deployment's security and efficiency.
We encourage you to practice these techniques and explore further configurations to suit your specific needs. Feel free to leave your thoughts and questions in the comments below. Don't forget to share this article with others who may find it useful, and explore more content on our website for additional insights into IoT and cybersecurity.
References:
- OpenSSH Documentation: https://www.openssh.com/manual.html.
- NIST Cybersecurity Framework: https://www.nist.gov/cyberframework.